Android malware attack relays NFC data from your card to thief standing at an ATM wiping you out
Discovered by cybersecurity firm ESET, the firm named the malware NGate because the NFCGate toolkit used to analyze NFC traffic is employed by the attackers. Czech police busted up a gang using a similar scheme after arresting one of the members withdrawing cash out of an ATM machine in Prague. Here is how the scam operated. The victim would receive a text urgently demanding that they install an app because of an issue with their tax return. This text would contain a link to a fake website that collected the victim’s credentials
giving the attacker access to the target’s bank account.
The victim would then receive a phone call from the attacker pretending to be a bank employee. The banking customer would be told that a text was being sent to him with a link to an app that would be used to protect his account by allowing him to change his PIN number and verify his card. The victim is asked to enable NFC on his phone and to scan the card. The mobile app was actually NGate malware.
The malware can relay NFC data from the victim’s card through a compromised smartphone to the attacker’s smartphone which can then emulate the card. As a result, the criminal would receive the information in real time and withdraw money from an ATM. It’s scary, to be sure.
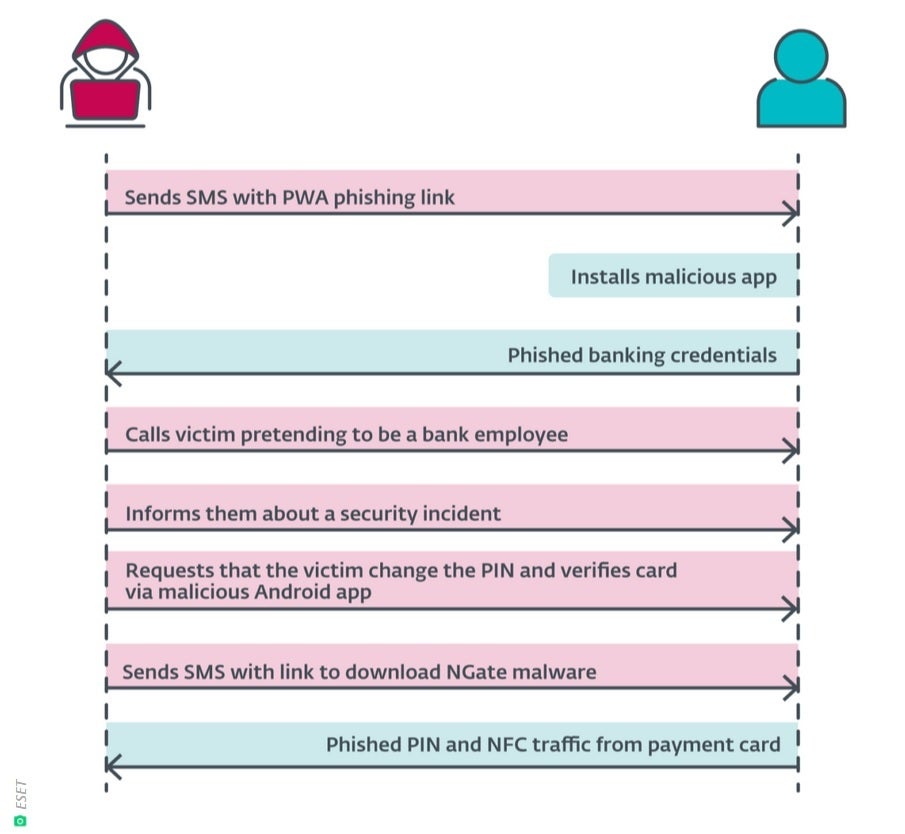

How the NGate malware attack works. | Image credit-ESET
“Based on our current detections, no apps containing this malware are found on Google Play. Android users are automatically protected against known versions of this malware by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play.”-Google
Google said that no such malware was found in apps listed in the Play Store. Google noted that its Play Protect feature warns users and blocks apps showing malicious behavior even if those apps come from third-party sources. Six NGate laden apps were discovered from non-Play Store sources between November and March that attacked three Czech banks.
How can you make sure that you don’t become a victim? Never send personal information including PIN numbers online. Even if it seems that the text or email you received is legit, just do not hand over any personal data. Always assume that you’re being scammed. Confirm requests for information by calling the company requesting it. Get the phone number from Google, do not call the number listed in the text.
Source link



